
Bot management refers to bot detection as well as the blocking of undesired or malicious internet bot traffic, all while still allowing useful bots to access web APIs and properties. It may deploy mechanisms such as allowing and blocking lists, rate limiting, and bot traps to mitigate the risk and damage of bot attacks.
As internet traffic becomes more bot-driven, comprehensive bot management provides the best defense against numerous automated threats—such as application-layer distributed denial-of-service (DDoS) attacks, SQL injection risks, and spam campaigns—that can harm business applications.

The solution
Why is bot management necessary?
The same fundamental features that make good bots so useful also make bad bots threatening.
A bot can automate a broad spectrum of activities, ranging from crawling for purposes of search engine indexing to supporting real-time customer service chats. But this efficient automation can be leveraged for scalable and highly effective cyberattacks, too. Common examples include:
- DDoS attacks: A coordinated botnet can receive and execute instructions for overwhelming its targets with junk traffic. Advanced Layer 7 DDoS attacks use bots that appear to be sending legitimate requests.
- Vulnerability scanning and probing: Malicious bots may continuously look for vulnerabilities in internet-facing web applications and APIs. If found, any weakness can be exploited by cross-scripting (XSS), SQL injection, and related bot-dependent attacks.
- Account takeover: Bots may be used in credential stuffing and password spraying attacks, both of which involve attempting to break into accounts by brute-force guessing—a task to which bot-driven automation is naturally suited.
- Spam and malware distribution: The automation of a botnet can fuel massive spam operations that deliver malware to countless inboxes. Phishing attacks can be scaled using botnets capable of sending billions of such messages every day.
To mitigate these risks and others, modern bot management solutions perform bot detection through IP address analysis, bot signatures, device fingerprinting, and behavioral analysis. Bot management solutions enable you to reliably defend your web applications and APIs from every type of bot attack, from a basic attempt at password spraying to a highly sophisticated botnet-powered DDoS campaign.
How does bot management work?
Multiple bot detection techniques are supported by modern bot management solutions:
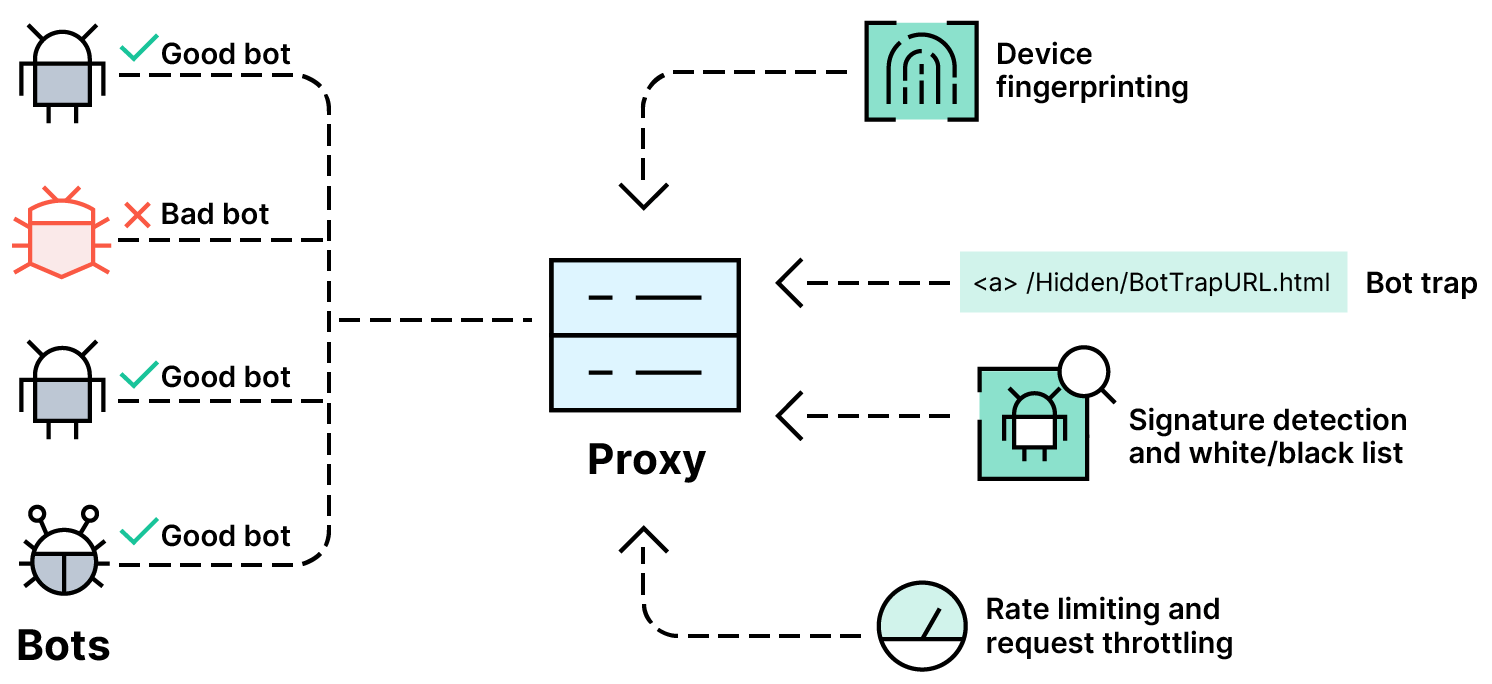
Bot signature files and profiles: A bot management platform maintains an active, up-to-date list of known bots and their signatures, which can be added to bot profiles for more reliable bot protection. By drawing upon this information, bot management solutions can then identify anomalous bot activity on the network and block it before it accesses and attacks important applications and/or APIs.
Transactions per second (TPS): Bot activity can be detected through TPS. By setting a time interval, bot management solutions can flag incoming traffic if the number of requests and the percentage increase in traffic exceed that parameter.
Malicious IP address blocking and IP reputation analysis: How can you accurately score the risk from a given bot and its requests? The regularly updated list of malicious IP addresses in bot management solutions makes doing so much more straightforward. IP reputation analysis also lets you know if a bot originates from a risky domain with a history of being involved in cyberattacks.
Device fingerprinting: With bot management, you can deploy multiple forms of behavior-based bot detection and control, including device fingerprinting. A device fingerprint identifies a client as a unique entity, based on attributes such as its IP address, screen resolution, browser attributes, HTTP request headers, and installed fonts. This fingerprint in turn can be used to block malicious yet legitimate-seeming bad bots as necessary.
Bot traps: A trap URL may be configured to identify malicious bot activity. The URL is advertised in the client response, but it is invisible to human users and not accessed by good bots. A common use of bot traps is to catch bad bots that have ignored a site’s robots.txt file and are attempting to scrape content or send spam traffic.
Together, these bot detection techniques enable bot management tools to manage and log bot traffic in accordance with bot policy rules, with support from various mechanisms.
Rate limiting and related traffic controls
Using the traffic management features in a bot management tool, it’s possible to set limits on designated bot traffic and prevent bad bots from entering the network, even if they have made it past other detection mechanisms. For example, an unknown bot that is not contained on either an allow list or a block list can be rate-limited so it cannot overwhelm an API or microservice architecture. Bot management solutions may also redirect and drop bot traffic once it’s flagged by any of the above detection techniques.
CAPTCHA enforcement
Bot management software may enforce a CAPTCHA to determine whether traffic is allowed to reach a domain. CAPTCHAs are useful for determining if traffic is human- or bot-directed, helping stem the flow of automated malicious bot activity that can comprise web applications and APIs. Traffic that fails to complete a CAPTCHA may be dropped or subjected to additional verification actions, including allow and block lists.
Allow list and block list deployment
Setting up allow lists and block lists for specific bots is an effective route toward ensuring that good bots are allowed to access web apps and APIs, while bad bots are kept at bay. Each allow list or block list can be customized to include particular IP addresses, subnets and policy expressions, enabling you to determine if a bot’s origins are acceptable.
Reporting and follow up
A bot management tool can provide analytics about average bot transaction requests per second, bot-to-human ratios for virtual servers, bot severity ratings and geographic origins and event histories of when bot signatures were added and updated. This information is valuable for fine-tuning the overall range of actions in a bot management strategy.
NetScaler for bot management
NetScaler bot management works together with NetScaler Web App Firewall (WAF) and API security capabilities to provide holistic protection from malicious bots.
Through the aggregation of data collated from bot management servers and ADCs, NetScaler provides comprehensive security for monolithic and microservices-based applications.
Get started with NetScaler
Request a demo or talk to sales
1-866-NetScaler